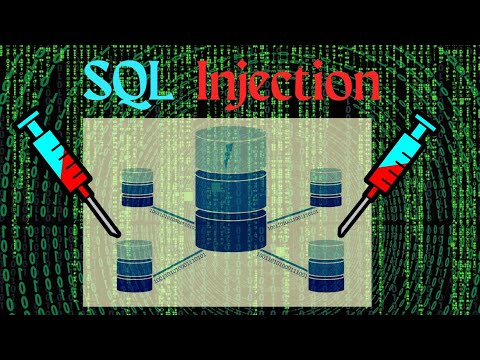
In this comprehensive tutorial, we delve into the fascinating world of SQL injection attacks. Follow along as we explore the vulnerabilities in DVWA, a purposely vulnerable web app, using Kali Linux and Metasploitable. Learn how to identify and exploit SQL injection vulnerabilities, and discover effective mitigation techniques. Whether you’re a beginner or an experienced pentester, this video has something for everyone!
🔗 Useful Links:
• What is SQL Injection: https://owasp.org/www-community/attacks/SQL_Injection
• SQL Injection Prevention: https://cheatsheetseries.owasp.org/cheatsheets/SQL_Injection_Prevention_Cheat_Sheet.html
The contents of the video.
0:00 – Introduction to SQL Injection
0:39 – What is SQL injection?
1:39 – What is a blind SQL injection?
2:45 – Hands-on SQL injection
03:30 – How to set up DVWA for testing?
05:00 – SQL injection scenario
6:35 – See all users in a database DVWA SQL injection
9:23 – How to prevent SQL injection?
10:48 – Conclusion of SQL injection, DVWA
👍 If you find this exploration fascinating, don’t forget to hit the like button, subscribe @thatcyberguyofficial for more tech insights, and share with your fellow tech enthusiasts to stay up to date with our latest videos. Let’s build a safer and more resilient connected world together!
.Follow-us & Stay in Touch:
https://www.facebook.com/thatcyberguyofficial
https://www.instagram.com/thatcyberguyofficial
https://www.x.com/thatcyberguy_
https://www.thatcyberguy.com
#sqlinjection
#cybersecuritytutorial
#injectionattack
#cybersecurityexplained
#cybersecurity